 |
| DOS And DDOS Attack |
What is a DOS attack?
In a denial-of-service (DoS) attack, a malicious actor tries to make a computer or other device unavailable to the users for whom it was intended by interfering with normal operation. DoS attacks usually work by flooding a targeted machine with requests until normal traffic cannot be processed, which denies service to additional users. One of the characteristics of a DoS attack is that it is launched from a single computer.
How does a DoS attack work?
A DoS attack's main goal is to overload the capacity of a target machine in order to deny service to additional requests. By their similarities, the various DoS attack vectors can be categorised.
DoS attacks are of typically 2 categories:
Buffer overflow attacks
A kind of attack where a memory buffer overflow can cause a computer to use up all of its memory, hard disc space, or CPU time. This kind of exploit frequently causes slowness, system crashes, or other harmful server behaviors, which leads to denial-of-service.
Flood attacks
A malicious actor can oversaturate a server's capacity and cause denial-of-service by bombarding a targeted server with an excessive number of packets. Most DoS flood attacks require more bandwidth than the target in order for the malicious actor to be successful.
What are some historically significant DoS attacks?
DoS attacks have historically taken advantage of security flaws in network, software, and hardware architecture. As DDoS attacks have a greater disruptive potential and are relatively simple to create given the tools at hand, these attacks have decreased in frequency. The majority of DoS attacks can actually be converted to DDoS attacks.
A few common historic DoS attacks include:
- Smurf attack: a previously exploited DoS attack in which a hacker sends spoof packets to a targeted IP address using the broadcast address of a network that is vulnerable.
- Ping Flood: This straightforward denial-of-service attack, known as a "ping flood," works by bombarding a target with ICMP (ping) packets. Denial-of-service can occur by bombarding a target with more pings than it can effectively respond to. The use of this attack as a DDoS attack is also possible.
- Ping of Death: Frequently confused with a ping flood attack, a ping of death attack entails sending a malicious packet to a targeted machine, which causes negative behaviour like system crashes.
What is a DDoS attack?
A distributed denial-of-service (DDoS) attack is a malicious attempt to obstruct a server, service, or network's regular traffic by saturating the target or its surrounding infrastructure with an excessive amount of Internet traffic.
By using numerous compromised computer systems as sources of attack traffic, DDoS attacks are made effective. Computers and other networked resources, such as IoT devices, can be exploited machines.
When viewed from a distance, a DDoS attack resembles an unexpected traffic jam that blocks the highway and keeps regular traffic from reaching its destination.
How does a DDoS attack work?
DDoS attacks are conducted using networks of computers connected to the Internet.
These networks are made up of computers and other devices, such as Internet of Things (IoT) devices, that have been infected with malware, enabling an attacker to remotely control them. These particular devices are known as bots (or zombies), and a botnet is a collection of bots.
Once a botnet has been created, the attacker can control an attack by giving each bot remote instructions.
Each bot in the botnet sends requests to the IP address of the victim's server or network when that server or network is being targeted by the botnet. This could overload the server or network and result in a denial-of-service attack on regular traffic.
It can be challenging to distinguish attack traffic from regular traffic because each bot is an actual Internet device.
What is the difference between a DDoS attack and a DOS attack?
The quantity of connections used in the attack is what distinguishes DDoS from DoS. The effectiveness of some DoS attacks, such as "low and slow" attacks like Slowloris, can be attributed to their simplicity and need for few resources.
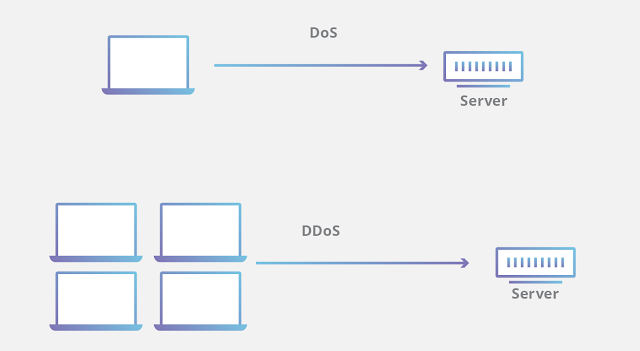 |
| Difference between DOS and DDOS Attack |
DoS attacks use a single connection, whereas DDoS attacks use multiple attack sources, frequently in the form of a botnet. In general, many of the attacks share fundamental similarities and can be carried out using a variety of malicious traffic sources. Discover how Cloudflare's DDoS defense prevents denial-of-service assaults.
